Small businesses aren’t “beneath the hackers’ radar.” Automated attacks don’t care about your headcount, and the fallout is real. In the UK, half of businesses reported at least one cyber breach/attack in the last 12 months, and 22% experienced cyber crime (phishing dominates). Average direct annual cost per victim business: ~£1,120. That’s before reputational damage or lost productivity.
1) The human factor is the main door in
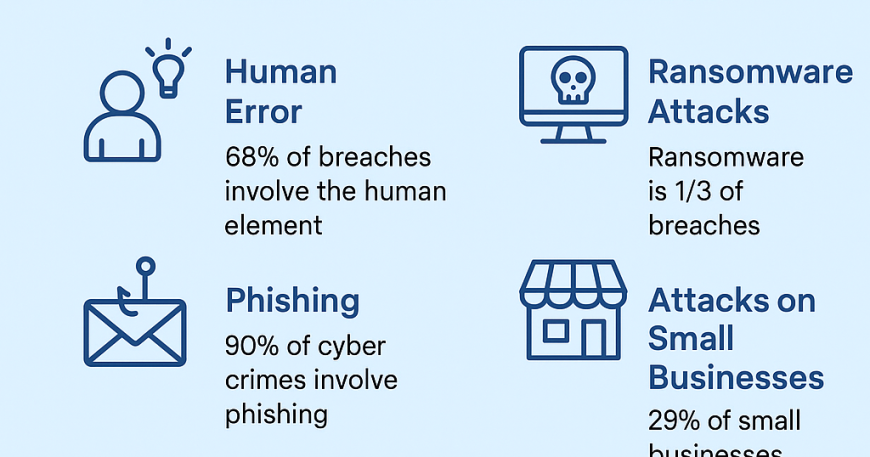
Across breaches globally, the human element features in 68%—things like phishing clicks, credential reuse, and misdirected emails. Translation: user mistakes and weak processes keep paying attackers’ bills.
Action that moves the needle: Turn on MFA everywhere you reasonably can. Microsoft’s data shows MFA blocks ~99% of account-compromise attempts. Cheap. Boring. Ridiculously effective.
2) Ransomware & extortion aren’t “big company only”
Ransomware plus related extortion tactics now account for roughly one-third of breaches; ransomware alone is a top threat across 92% of industries. Negotiation data shows median ransom demands equal about 1.34% of company revenue—that can be fatal for an SME’s cash flow.
3) Phishing is the everyday headache
In the UK, among organisations that suffered cyber crime, ~90% report phishing—it’s the most common entry point by far. If your team can spot and report dodgy emails, you’ve just removed the attacker’s easiest path.
4) “We’re small” won’t save you (and monitoring gaps hide problems)
UK data shows 29% of small businesses and 19% of micro businesses experienced cyber crime in the last year—lower than medium/large firms, but that’s likely under-detection, not immunity. Smaller orgs typically have fewer monitoring tools, so more slips by unnoticed.
5) Prevention is cheaper than recovery
UK businesses hit by cyber crime report mean direct costs around £1,120—and that excludes many soft costs (downtime, lost sales, higher insurance, legal). For small firms, even a short outage hurts.
Quick checklist you can act on this week
- Turn on MFA for email, VPN, admin, and any external apps.
- Kill unused accounts; review admin rights.
- Patch internet-facing stuff first; remove risky remote tools.
- Enable email authentication (SPF/DKIM/DMARC) and train staff to report phishing.
- Test restores from backups (don’t just assume they work).
- Write a one-page incident plan with who to call and first steps. (Most SMEs don’t have one.)